May 7, 2024
Securing email systems against fraud and misuse is paramount. Email security is one of those things that generally goes undiscussed – we just expect it to work. Over the years though, email security has had to play catch up.
One of the foundational tools in this effort has been the Sender Policy Framework (SPF), which allows email domain owners to specify which mail servers are permitted to send email on behalf of their domain. While SPF has been instrumental in reducing email spoofing, it alone is no longer sufficient due to its limitations, such as only verifying the sender’s return path and not the header from the address which is often displayed to the user. This gap has necessitated the development of additional protective measures like Domain-based Message Authentication, Reporting & Conformance (DMARC), DomainKeys Identified Mail (DKIM), and the emerging technology Brand Indicators for Message Identification (BIMI).
Let’s jump in to explain these technologies and their critical roles in modern email security strategies.
Understanding SPF: The Foundation of Email Authentication
Sender Policy Framework (SPF) is a security mechanism designed to prevent spammers from sending messages on behalf of your domain. With SPF, an organisation lists all the mail servers authorised to send mail on its behalf in the DNS records. When an email is received, the recipient’s mail server checks this record to confirm that the email comes from a listed server. If not, the email can be marked as spam or rejected outright.
However, SPF has its limitations. It only checks the envelope part of the message, which includes the return path but not the ‘From’ address displayed to the end-user. Therefore, while helpful, SPF alone does not fully prevent impersonation, where attackers can spoof a visible email address to deceive the recipient. You’ve likely seen a lot of this over the years with emails pretending to be Xero Support <someweirdemail@someweirdwebsite.ru>.
The Role of DKIM in Combatting Email Spoofing
To enhance the security measures SPF provides, DomainKeys Identified Mail (DKIM) adds a layer of verification that involves attaching a digital signature to outgoing emails. This signature is linked to the sending domain and is verified against a public cryptographic key in the sender’s DNS records. Successful verification ensures that the parts of the email protected by the signature have not been altered in transit, confirming the sender’s identity and increasing the trustworthiness of the message.
Strengthening Policies with DMARC
Domain-based Message Authentication, Reporting & Conformance (DMARC) combines the features of SPF and DKIM, providing a robust mechanism for email authentication. DMARC allows domain owners to define a policy instructing recipient mail servers on handling emails that fail SPF or DKIM checks. Choices include reporting the incident to the sender, quarantining the message, or outright rejecting it. This not only helps in preventing email fraud but also provides domain owners with critical feedback on the source of attacks and misuse.

Introducing BIMI: Enhancing Trust Through Visual Identification
Brand Indicators for Message Identification (BIMI) represent a significant advancement in email authentication technology. BIMI allows organisations that have implemented DMARC to augment verified emails with their brand’s logo, making it easier for recipients to identify genuine messages. This visual cue helps to build trust and improve user engagement, while also incentivising companies to adopt strict email authentication standards to qualify for BIMI.

The Importance of Monitoring Email Authentication Technologies
In the majority of businesses where we’ve taken over IT support and management, we’ve found that monitoring of these key technologies is absent.
Monitoring the implementation and efficacy of SPF, DKIM, DMARC, and BIMI is crucial for maintaining secure email communication channels. Regularly reviewing authentication failures through DMARC reports helps in identifying and addressing security vulnerabilities, ensuring that protective measures are functioning as intended, and adapting to the evolving landscape of email-based threats.
Monitoring can also provide insight into why emails might be rejected when sending out newsletters, or other types of automated emails that originate from your domain.
Conclusion
While SPF provides a fundamental base for email authentication, additional layers such as DKIM, DMARC, and BIMI are essential to effectively combat sophisticated email threats and build trust in digital communications.
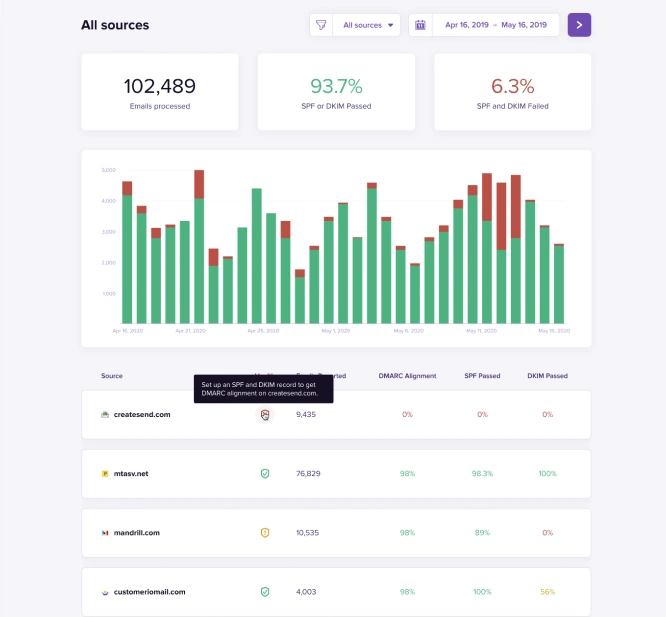
Implementing DMARC monitoring significantly enhances an organisation’s ability to manage and secure its email communications. Such tools provide a comprehensive view of all email activities under the organisation’s domain, including detailed reports on both compliant and non-compliant emails. This visibility is crucial for identifying potential vulnerabilities and unauthorised email sources.
By using DMARC monitoring, organisations can streamline the process of analysing DMARC reports and alerts. These tools automate the interpretation of complex XML feedback, transforming it into user-friendly charts and actionable insights. This means that security teams can quickly identify issues, understand email flow patterns, and make informed decisions about their email security policies.
DMARC monitoring also aids in optimising email deliverability. By ensuring emails are authenticated against DMARC protocols, organisations can improve their sender reputation. A better reputation reduces the likelihood of emails being flagged as spam, thereby enhancing the reliability of email communications with clients and partners.
In essence, DMARC monitoring not only fortifies security but also enhances operational efficiency and communication reliability, making it an indispensable asset for any organisation serious about safeguarding its email integrity.
At Layer3, we are dedicated to implementing, monitoring, and optimising these technologies to safeguard your email interactions and ensure your organisation’s communication remains secure and reputable.

